WHAT IS THE BLOG ABOUT?
- WHY DYNAMIC VULNERABILITY MANAGEMENT IS VITAL
- WHAT IS THE AN EFFECTIVE SOLUTION LIKE
- HOW CISCO'S KENNA.VM WORKS
Data security, vulnerability management, prevention
Of course, this is easier said than done, as an average large company has up to thousands of assets and millions of vulnerabilities, and dozens of new ones are discovered every day. It is reassuring that less than two percent of the vulnerabilities are being actively exploited from the dark side. But even two percent of the millions of vulnerabilities are more than IT security and operation teams can handle. Therefore, a responsible company needs a solution that processes all the internal security data, analyzes it with billions of external data, and then tells you which vulnerabilities pose the greatest risk to the enterprise infrastructure. This solution comes from Cisco, it’s Kenna.VM.
INSTEAD OF TIME-CONSUMING SOLUTIONS: KENNA.VM
Applying Kenna Security you can deploy an easy-to-use system for the processing of IT infrastructure information and security data, that eliminates the need for IT professionals to analyze vulnerabilities in spreadsheets. With this solution, you no longer have to waste valuable time searching for individual vulnerabilities on the Internet to assess their severity. There is no need to waste resources on troubleshooting or remediation with inadequate methods. This is because the IT security team will finally be able to evaluate and rank vulnaribilities based on the real risks, and to carry out repairs, maintenance and possibly improvements in the light of these.
Kenna.VM is a scalable, cloud-based solution that provides the most up-to-date and accurate risk priority available, enabling IT security and operations teams to take a risk-based approach to managing vulnerabilities by prioritizing and proactively managing key vulnerabilities.
AND ONLY KENNA.VM IS ABLE TO SERVE IT?
We can’t say there aren’t competitors to the solution, but we did say that last year, in 2021, Kenna Security won the Cutting Edge in Vulnerabilty Management at the 9th Annual Global InfoSec Awards at #RSAC 2021. And it’s because of that, the solution combines 18+ threat and exploit intelligence feeds, 7+ billion managed vulnerabilities, global attack telemetry, and recovery intelligence to accurately track and measure real exploitation activity on the company’s global attack surface. Using predictive modeling technology, Kenna.VM can also accurately predict the future risk of vulnerabilities as they are discovered, allowing organizations to proactively manage risk.
HOW DOES KENNA SECURITY'S SOLUTION WORK?
This is a fairly complex solution, so it would be difficult to describe it all briefly, but we will try to gather the points that make it worthwhile for any medium and large business to consider using it.
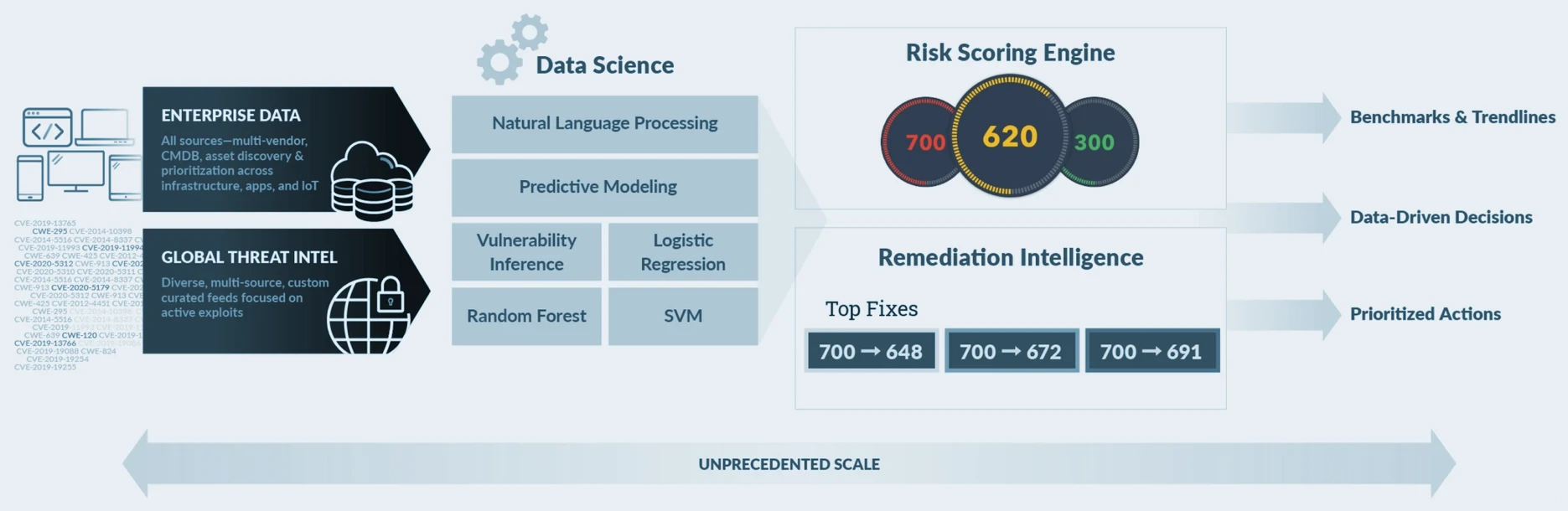
Combines external and internal data in a single risk view
Using machine learning and data science, the Kenna solution processes and analyzes 18+ threat and exploitation intelligence feeds, more than 12.7 billion managed vulnerabilities, and company security data to provide an accurate picture of the company’s risks. By risk scoring & remediation intelligence, the IT security management can get information needed to make remediation decisions.
Brings together all data from the multi-vendor IT security environment
The Kenna solution is prepared for the fact that every IT environment is different. That’s why it has more than 55 pre-installed connectors for more than 30 manufacturers. This allows the solution to provide the widest possible overview of risks across in the entire security stock, from vulnerability checkers to SAST, DAST, SCA security testing tools, bug programs, and configuration management databases. If a connector doesn’t exist, Kenna Data Importer lets you create your own connector. A couple of popular connectivity options.
Presents the threat in detail
Gathering security data is just the first step. You also need to understand what attackers are doing, how they are doing it, and what tools they are using to exploit the vulnerabilities. That’s why Kenna collects and analyzes data from external threat and exploitation feeds, as well as a unique database of more than 7 billion managed vulnerabilities, to uncover what attackers are doing in real time.
Predicts and prevents exploits
The better the more data is analyzed. Kenna uses natural language processing, predictive modeling, and other data science techniques to assess, rank, and predict risks. With predictive modeling, Kenna can predict the vulnerability of new vulnerabilities with 94% accuracy. Natural language processing analyzes the elements of vulnerability and threat data that are in human-readable text. And other predictive technologies help build the Kenna risk score.
Creates a common language for setting risk priorities
Kenna’s intelligent risk score engine actually creates a “common language” for IT security and operations to assess vulnerabilities. The risk score factors in the number of instances of each vulnerability in your environment, their potential severity, and the assets that are threatened as a result of each vulnerability. Then displays a number between 0-1,000, with 0-330 being lowest risk, 331-660 in medium and 660-1,000 as high risk for the group of assets associated with that risk meter, or asset group.
Helps you identify the vulnerabilities that need to be fixed first
Kenna’s recovery intelligence, by determining risk scores, provides insight into which vulnerabilities pose the greatest risk to an organization. These are the vulnerabilities that decrease the most when scoring risk scores. Because vulnerabilities are ranked based on the smart risk score engine recommendation, for example, not just the number of devices involved, these recommendations increase efficiency across all vulnerabilities.
Prioritized, data-driven interventions and decisions
Nothing compares to a completely personalized security insight. Through customizable, access-controlled asset group management, Kenna provides a flexible and quantifiable picture of your organization’s risk situation. Managing and reporting vulnerabilities at the individual asset group level allows the IT team to confidently correct reliable, science-based information. Detailed, holistic reports and benchmarks help align the organization and enable management to make data-driven decisions about the use and development of security resources.
CONCLUSION
Kenna Security makes it extremely easy to continuously and thoroughly examine vulnerabilities in your enterprise infrastructure by comparing data from internal and countless external locations. It provides management with data-driven, intelligence-based information and suggestions to reduce the vulnerability of the organization. The point is to reduce the human resources and thus the expenditure associated with vulnerability management processes, to centralize up-to-date information, and to prevent and avoid the losses they cause.