WHAT IS THE BLOG ABOUT?
- What is a post-breach solution?
- HOW DOES IT RECOGNIZE THREATS?
- Functionality and capabilities
Endpoint Protection, Post-breach, Threat and Vulnerability Management
Microsoft 365 provides access to a wide range of security tools and features to help protect your organization, but many advanced tools are found only in Microsoft 365 E5. The extended endpoint protection package (P2) is also available only in E5, including the following features:
- Endpoint detection and response
- Automated investigation and remediation
- Threat and Vulnerability Management
- Intelligent threat detection (threat statistics)
- Test environment (in-depth analysis)
However, the blog is not about the differences between the packages, but about the versatility of the solution itself, the benefits of using it in a general Windows environment.
And that’s why we’re even mentioning one important thing. It is no accident that Microsoft renamed the product. The purpose was to reflect the fact that it is now available to protect endpoints using operating systems other than Windows, such as macOS, Linux, iOS, and Android.
WHAT IS ENDPOINT PROTECTION?
Briefly, Microsoft Defender for Endpoint automatically detects and fixes advanced attacks on your endpoints. It examines the scope and potential impact of each threat, generating reports on various threats on the organization’s machines, enabling quick and easy mitigation and removal of threats using advanced tools and automation.
We must emphasize that Microsoft Defender for Endpoint is not an antivirus (AV) product. Microsoft Defender – not to be confused with Microsoft Defender for Endpoint – provides malware and antivirus capabilities for the latest Windows operating systems, while Defender for Endpoint is a post-breach solution that complements Microsoft Defender AV.
What is a post-breach solution?
The aim of integration of a post-breach solution into IT security infrastructure is to provide assistance after a security incident was breached. Why is this important? Because the “Zero Trust Strategy” is a best practice – it is a modern cyber security model that starts from the assumption that an incident can and will happen at a certain point in time. Given that no security solution in the world is impenetrable, Zero Trust is the most logical and appropriate approach.
Microsoft Defender for Endpoint ensures that an incident, a malicious code can be quickly isolated and managed as it occurs before it causes any damage or spreads within the network.
It also identifies vulnerabilities in your organization, such as out-of-date softwares, and provides repair options to address them. Microsoft Defender for Endpoint is therefore preventative and offers an advanced level of protection for IT networks.
HOW DOES DEFENDER FOR ENDPOINT WORK?
Endpoint protection is agentless and does not require installation or on-premise infrastructure as it can be operated in the cloud. The technology uses “endpoint behavior sensors” that are located in the operating system of each device. These Windows sensors continuously collect data and transmit it to the organization’s own cloud instance of Microsoft Defender. Microsoft Defender for Endpoint then analyzes the behavior of code running on your organization’s machines to determine if it could pose a threat.
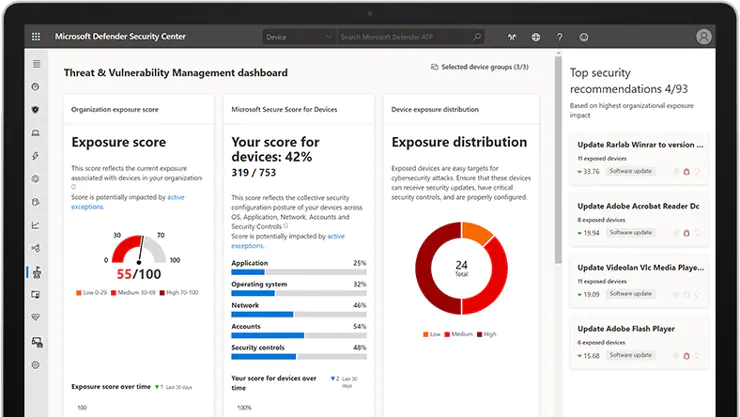
HOW DOES IT RECOGNIZE THREATS?
Microsoft basically collects an incredible amount of telemetry data from customers worldwide – more than 8 trillion data signals a day. This telemetry consists of data from Microsoft services such as Microsoft Defender for Endpoint, Office 365 for Endpoint, and data from Microsoft cybersecurity teams and global law enforcement. Microsoft refers to this data set as the “Microsoft Intelligent Security Graph.” Microsoft runs cutting-edge machine learning, artificial intelligence, and great data analytics on this telemetry. This amount of data allows Microsoft to determine how well the behavioral patterns in the code are considered “normal” and what patterns of behavior may indicate malicious activity, such as malicious code or other types of attacks. Insights from the Intelligent Security Graph provide real-time protection against threats in Microsoft products and services, including Microsoft Defender for Endpoint.
- 400,000,000,000 emails analyzed
- 100,000,000+ Windows device updates
- 700,000,000 Azure user accounts analyzed
- 450,000,000,000 authentication analysis per month
If organizations faced threats, this information is fed back into Microsoft’s cloud, which learns which of these behaviors indicates a threat. If it detects a threat within Microsoft Defender for Endpoint, it scans all devices in organization for threats and provides guidance:
- how the threat started,
- exactly what the threat is,
- and also what the threat is likely to do within the organization
SecOps can then take action to resolve the threat and fix the problem, and in some cases, use automatic fixes performed by Microsoft Defender for Endpoint.
Functionality and capabilities
While key features of Microsoft Defender are tightly integrated and intertwined with other Microsoft cybersecurity products, Microsoft Defender for Endpoint’s capabilities can be broadly summarized into the following categories:
Dealing with threats and vulnerabilities
Defender for Endpoint performs a real-time software inventory of endpoints. Therefore, you can see all the software on your machine and get an insight into the changes, such as patches, installations, and uninstallations. Where there are known vulnerabilities in the applications running on your computer or missing fixes, Microsoft Defender for Endpoint will list them, rank them, and fix them with security suggestions. Integration between Microsoft Defender for Endpoint, Intune, and System Center Configuration Manager (SCCM) provides a built-in repair process.
Reduction of attack surface
With Defender for Endpoint, you can also configure certain controls to minimize areas where cyber threats are a real threat. For example, applications must be marked as trusted in order to run, instead of being trusted by default. Hardware isolation also reduces the attack surface, isolating untrusted Web sites and PDFs inside lightweight containers to keep them separate from the Windows operating system – protecting your machine and corporate data from intruders.
Endpoint Detection and Response (EDR)
The most important post-breach feature of Defender for Endpoint is its endpoint detection and response (EDR) capabilities. It detects attacks in near real time and provides effective alerts to IT and security analysts. Alarms with common characteristics (such as the same file, the same URL, nearby times, etc.) are automatically grouped as “Incidents”. This aggregation makes it easier for the SecOps group to investigate and respond to threats within the organization.
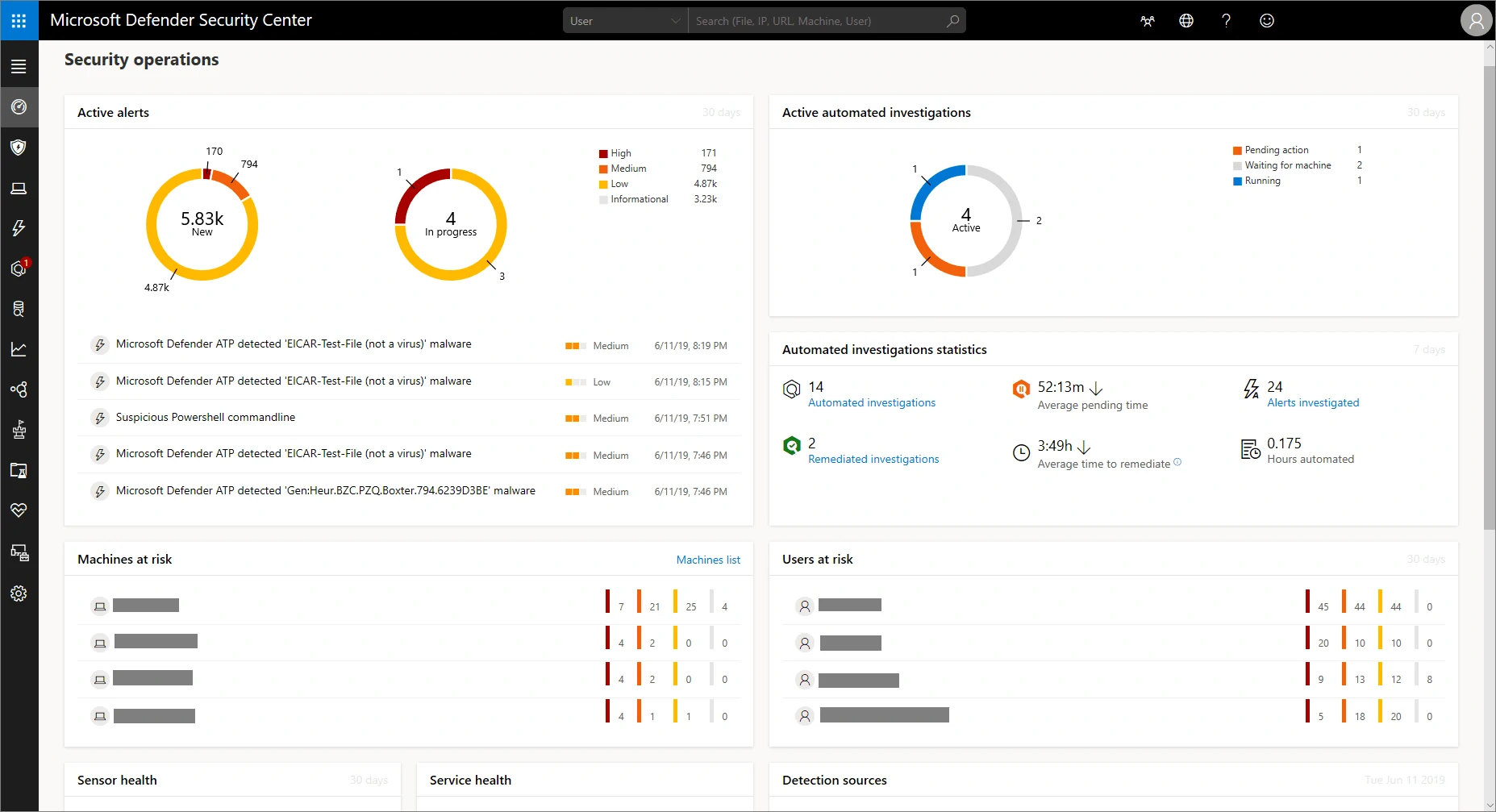
The Microsoft Defender for Endpoint security operations dashboard lets you view your organization’s data in one way from one central location. For example, you can view machines at risk, users at risk, suspicious activities, active alerts, automated scans on a dashboard, where company data, analysis, and recommendations are summarized.
Warnings / Alarms
If threats occur at endpoints, e.g. a malicious .exe file, the detection system notifies you almost immediately. The alert is displayed on the dashboard with various metadata such as address, affected machine name, user name, severity score and how long it has been in the queue.
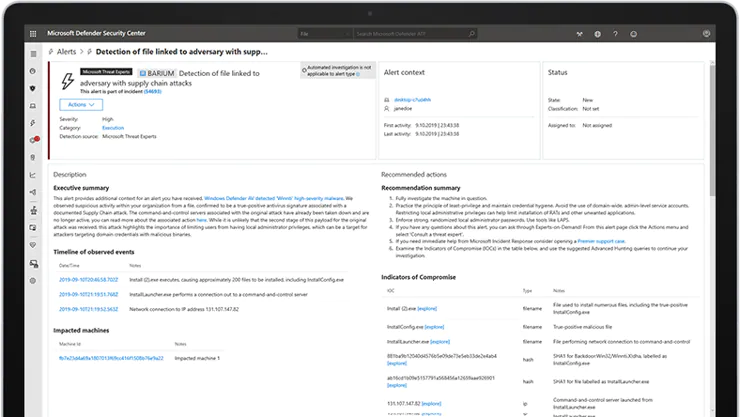
Investigation
The threat can then be further investigated. Defender for Endpoint provides a description of the threat, explaining what happened, e.g. suspicious behavior has been detected in Microsoft Word. The behavior may indicate that a Word document has been used to transmit malware or initiate other malicious activity on the machine. A list of suggested actions for the best approach to suspicious behavior also appears. While this is useful for removing the threat, SecOps also wants to know how and why the threat occurred.
One of the best features of Microsoft Defender for Endpoint is the timeline of events. Within the alert, you can open a timeline that appears in the form of a process tree structure and shows the full timeline of how the threat arrived at the endpoint and what activities it has been participating in since it appeared on the device.

Remediation
With Microsoft Defender for Endpoint, the SecOps team can respond quickly to attacks by taking response actions on machines and files They can then select which actions to perform. This could include running an antivirus, restricting application execution, or disconnecting the machine from the network while maintaining a connection to Microsoft Defender for Endpoint. It allows these machines to be remediated and inspected as well.
Microsoft Defender for Endpoint allows you to quickly add and quarantine files, and provides insight into how many machines are infected within the organization, and about the global prevalence of the file, and the number of copies of the file.
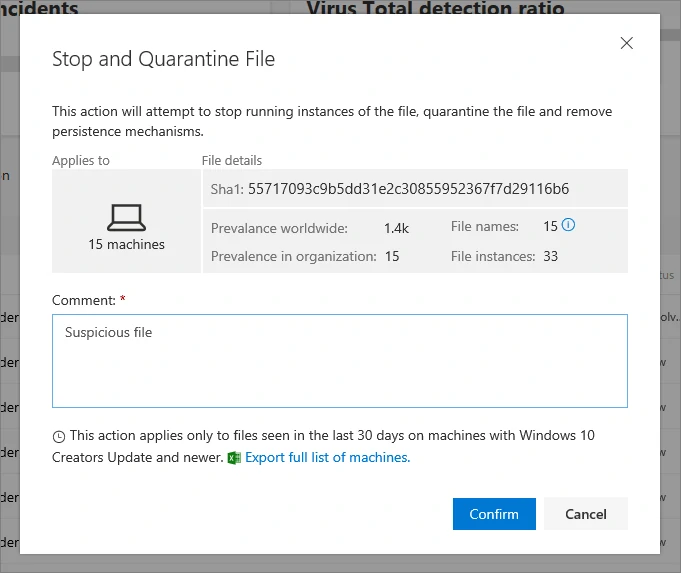
These insights are extremely valuable and allow organizations to successfully address threats extremely quickly.
Automated inspection and remediation
Due to the high prevalence of online threats and multiple endpoints within the organization, Microsoft Defender for Endpoint can generate a significant amount of alerts – which can be a challenge for IT teams to keep up with. Therefore, Microsoft Defender for Endpoint is part of an automated service that scans for alerts and resolves security incidents. This reduces the number of alerts, so security administrators can focus on the most pressing issues. Alternatively, you can work with a cyber security provider, such as Syswind, which can handle incoming alerts and highlight important priorities that require immediate action.
Advanced Hunting
With advanced hunting, Microsoft Defender for Endpoint makes powerful searches and queries available. Custom detection rules are used to generate alerts that appear in the central control panel of the Microsoft Defender Security Center.
Integrations
A Microsoft Defender for Endpoint mélyen integrálódik más Microsoft fenyegetésvédelmi termékekkel, teljes biztonsági megoldást nyújtva. Az integrációk a következőket tartalmazzák:
- Azure Advanced Threat Protection (Azure ATP)
- Azure Security Center
- Azure Information Protection
- Conditional Access
- Microsoft Cloud App Security
- Office 365 Advanced Threat Protection (Office 365 ATP)
- Intune
SUMMARY
Microsoft’s cyber defense system with Defender for Endpoint raises the bar in the fight against threats. Let there be no misunderstanding, this does not mean that security incidents cannot happen and that a certain incident can be escaped without any damage or loss of data. Microsoft’s system simplifies the work of the SecOps teams, and a lot can be automated, but the threats aren’t going away. The key to using it is to put security, remediation, and investigation easier for organizations.