WHAT IS THE BLOG ABOUT?
- MULTI-FACTOR AUTHENTICATION
- FIDO2 AUTHENTICATION
- DUO MOBILE AUTHENTICATION
Multi-factor Authetication, Cisco DUO MFA, FIDO2
In the IT sector, although rapid developments are taking place in some areas, there are still countless users who rely on browser-based password managers and, in the worst case, set weak or identical passwords on all platforms. Companies can also be classified among these users. This results in cybercriminals and hackers gaining access to your data much more easily.
Security solutions that protect the organization’s network, such as anti-virus systems and advanced firewalls, as well as continuous updates and vulnerability tests, are necessary elements of a security strategy. However, the use of multi-step authentication, i.e. MFA, is essential to strengthen a company’s security situation.
MFA is proven to protect company data, making it much more difficult for cybercriminals trying to phish to access confidential information.
However, according to statistics, only 26% of US companies use multi-factor authentication. Although 81% of security incidents can be traced back to stolen, weak passwords. However, MFA is already an integral part of our everyday life. Think about where they are present in different areas of our lives; consumer-oriented online services such as banking, but Google also offers such an option for accessing accounts.
AUTHENTICATION FACTORS FOR MFA SOLUTIONS
Multi-factor authentication can be enforced with 3 factors.
1.
KNOWLEDGE
The most common knowledge factor is the password. Another knowledge factor can be the PIN code and security questions (e.g.: What was the name of your high school?). These are becoming less secure as users can easily become victims of phishing attacks.
2.
OWNERSHIP
Ownership factors include hard tokens, soft tokens, and smart cards. To verify a user’s identity, they may receive a one-time password sent to a smartphone, a unique code generated by a physical token, or a smart card inserted into the device. By definition, login devices with unique identifiers used for login are also suitable for one of several factors.
3.
INHERITANCE
Also known as biometric data, the unique physical characteristics of each of us. This authentication factor includes fingerprint scanning, voice or face recognition, retina scanning and other methods. For example, special authentication can be done with the help of the heartbeat, just like with the scanning of human veins.
AND HERE’S A SHOCKING FACT ABOUT PASSWORDS
An average office worker would have to remember 27 passwords.
If we consider that a strong password consists of at least 10 characters, which should be used in the most random order, then 27 different passwords require a good amount of memory. Or a password management app that raises new security questions. But there is also the question of whether 27 passwords are really necessary.
In our opinion, it is not absolutely necessary, because security does not require 27 unique, strong passwords, but rather 27 secure logins. It is a security risk in itself for someone to memorize and store 27 passwords and to be able to enter them in any case, no matter where they try to log in. Nowadays, there are many solutions so that you don’t have to use passwords for logins.
CISCO DUO – THE BASIS OF TRUST
Passwordless authentication is now a reality. As with any new technology, achieving a completely password-free state will be a long journey for many organizations. The advanced solution of Cisco Duo can be a good companion for secure logins. It helps to navigate, shows the right direction. Cisco Duo can provide a helping hand to companies that want to implement phishing-resistant authentication or use a Zero Trust security strategy.
WHAT PASSWORD-FREE SOLUTIONS DOES DUO OFFER?
Duo’s passwordless architecture allows it to offer a flexible selection that meets the unique needs of businesses and organizations:
1.
FIDO2 compatible, phishing-resistant authentication
- Platform authenticators – TouchID, FaceID, Windows Hello, Android biometrics
- Roaming authenticators – security keys (e.g. Yubico, Feitian)
2.
Strong authentication with Duo Mobile authentication app
- Check registered device
- Duo Push for passwordless authentication
- Trusted browser settings
FIDO2 AUTHENTICATION
FIDO2 authentication qualifies as anti-phishing authentication because:
- Removes passwords or shared secrets from the login workflow. Attackers cannot “eavesdrop” on passwords or use stolen credentials available on the dark web.
- It creates a strong connection between your browser session and the device you are using. It only allows login from a device authenticated to the app.
- Ensures that authentication data (public/private key) can only be exchanged between the device and the registered service provider. This prevents you from logging into fake or phishing websites.

Using Duo and FIDO2 authenticator enables organizations to enforce phishing-resistant MFA in their environment. However, we understand that preparing the IT infrastructure to support FIDO2 can be expensive and is usually a long-term project for organizations. In addition, installing and managing third-part security keys is an additional IT cost that some organizations cannot immediately undertake.
Alternatively, using Duo Push for passwordless authentication offers a simple and cost-effective solution for many organizations to begin their passwordless journey without compromising security.
STRONG AUTHENTICATION WITH DUO MOBILE APPLICATION
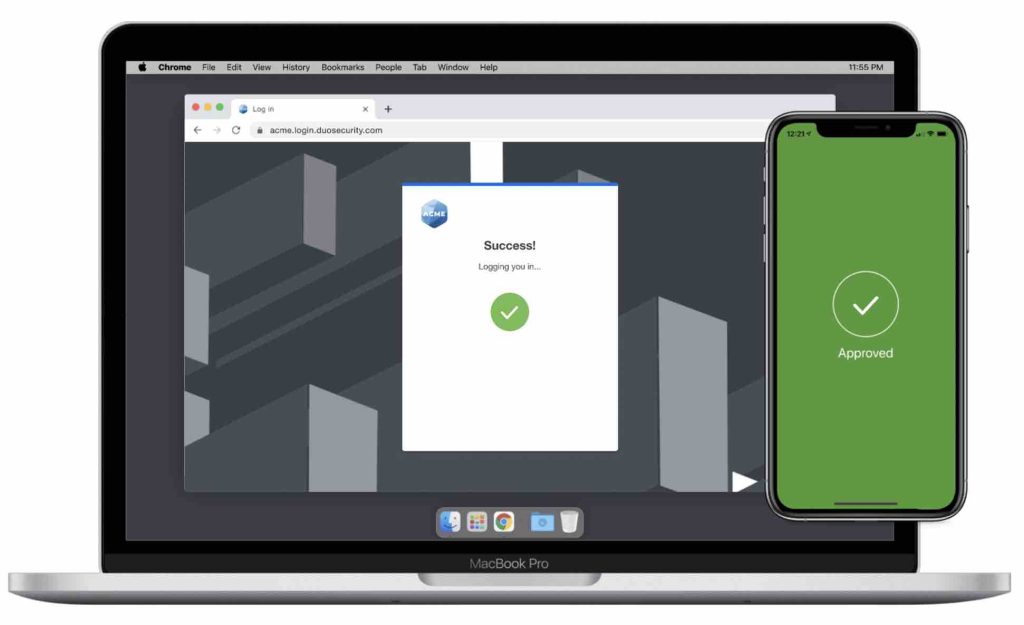
For passwordless authentication, Duo Mobile is multi-factor authentication itself. Upon receipt of a Duo Push notification, the screen lock of the mobile device must be unlocked to approve the request. In this process, the user can prove his identity by biometric identification and using the registered device.
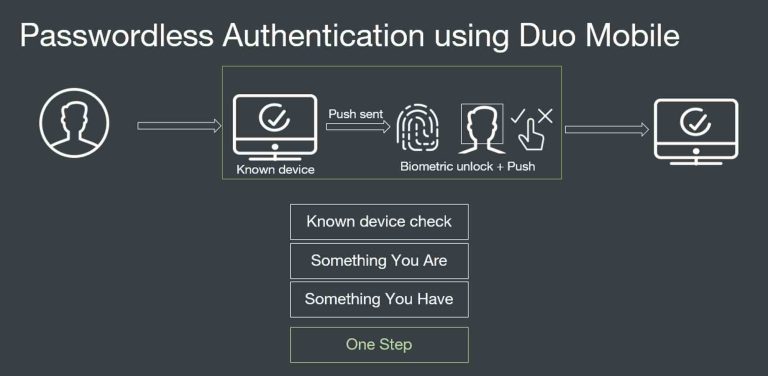
Additional security has been built into the login workflow to link the browser session to the device used to access the application. This mitigates phishing attacks that use tactics such as instant bombing of MFA. Duo achieves this in the following ways:
Check for known device:
After enabling the passwordless authentication policy, the user first successfully authenticates with multifactor authentication from an access device as a single sign-on process. This authorizes that access device to send a push notification for subsequent logins, ensuring that only known devices can send a passwordless notification.
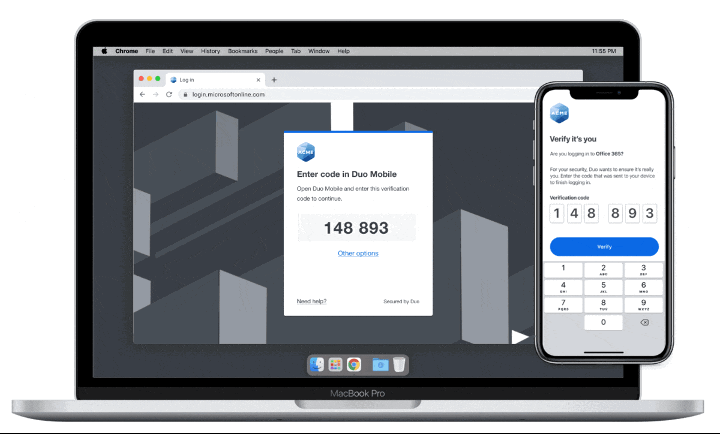
Duo Push for Passwordless:
The next time the user logs in, the user is automatically taken to a passwordless login workflow and a Duo Verified Push message appears, also requiring biometric authentication on the mobile device. This confirms the association of the device with user authentication.
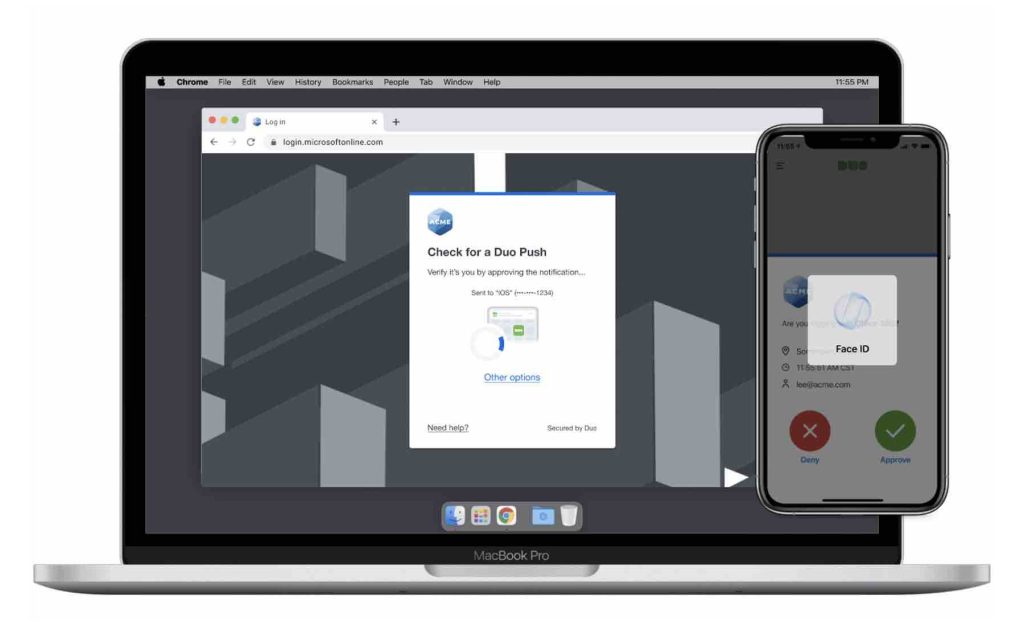
Trusted browser:
When authentication is complete, the user will be presented with “Do you trust this browser?” option. If the user chooses not to trust the browser, they will still receive a Duo Verified Push message for subsequent authentications. If the user chooses to trust the browser, a stronger association is established with the access device, the user then receives a standard Duo Push message along with the screen unlock. This reduces friction for users as we have sufficiently established trust in the login process.
Duo Push
- Approval based
- Low user friction
- Weak device binding
- Susceptible to MFA instant bombardment or MFA fatigue attacks
Duo Verified Push
- It is based on number matching
- Increases user friction
- Creates a more secure device association
- Reduces MFA instant bombardment or MFA exhaustion attacks
Duo Push for Passwordless
- Basically, the same as Duo Verified Push, but with biometric authentication
- It will change to Duo Push with biometric authentication if users trust the browser
- Creates a more secure device association
- Reduces MFA instant bombardment or MFA exhaustion attacks
SUMMARY
Today, IT managers have to consider many things when implementing a technology strategy. Cisco Duo, on the other hand, can help minimize the impact on everyday work by taking simple security steps. It provides an IT environment that is based on the Zero Trust model, but does not cause frustration for users. It simplifies the often-challenging password management processes and offers ready integration with increasingly popular passwordless login solutions.
Many companies have already started their password-free journey. If you also want to start your company on this path, ask for a professional consultation from our experts!