WHAT IS THE BLOG ABOUT?
- WHAT CYBER RESILIENCE RECOMMENDS
- WHAT ELEMENTS ORGANIZATIONS SHOULD FOCUS ON
- HOW TO EFFECTIVELY ADDRESS THE RECOMMENDATIONS
Cybersecurity, machine learning, artificial intelligence, cyber resilience
The technological concept basically defines the situation: everyone who has an Internet connection will suffer some kind of injury, attack, damage, so the business or operational processes and infrastructure must be designed and developed in such way that focuses to the resilience of the organization.
WHAT DOES CYBER RESILINCE RECOMMEND?
In the world of business and basic service providers, priority goal is to ensure the continuity of business operations. Its vulnerabiliy, unfortunately we have seen in series over the past few years in any part of the world, whether developed or less developed, can cause critical problems. In order to avoid these, the concept discusses in several points what technological and organizational developments are best addressed in a broader sense.
The first and perhaps most important element is the development of human resources. This is partly a cyber awareness development and partly an investment. In fact, it is forcing the creation of an educational platform such as for examlpe fire and accident prevention education, which is essential for any company.
It also makes suggestions for cooperation of organizations, especially the competition and the governmental sector, as it encourages the sharing and distribution of “best practice” methodologies. This is noticeably in its infancy in Hungary, but unfortunately we are not lagging behind, a couple of EU studies have warned about this, which we have discussed many times. The bottom line is that we have room for improvement in this area.
No less important is the provision of supply chains, which is also a critical issue that can only be achieved through deep cooperation. We have already discussed it too, as this topic cannot be repeated enough times, because the vulnerability of some products and services does not only have an impact on the revenue of specific businesses. In our opinion, this area has perhaps the fastest possibility of cooperation development – due to the strong interest of preserving capital and common corporate values.
On the other side are technology recommendations that require basic infrastructure improvements – from virtually anyone who doesn’t sell just hot dogs around the corner. We wouldn’t list how and what the oragnizations should start with. If you are interested, we offer a free pre-consultation – and of course, other IT security companies do too, where professionals could talk a lot about it. What the blog will be about – yes, it’s just starting – is measuring IT security and serving it with information, that is, maintaining a continuous and stable security operation.
The approach also focuses on state aid, the creation of research and development organizations, and emphasis on cooperation with the private sector. How this is going to happen in Europe or in Hungary, once we will see. For sure: it is always worth starting to prepair improvements of our systems on our side.
WHAT ELEMENTS SHOULD ORGANIZATIONS FOCUS ON?
So let’s take the parts of the recommendation that can be solved within a company.
- competence developoment
- efficient human resources
- cybersecurity system and operation
Education is an easy task on the to-do list, there are plenty of companies providing quality competency development – until cyber defense vocational education is spread in schools. What could be the problem with it? The fact that there are good students and worse ones everywhere. The latter, if they just don’t follow the rules for negligence or any other reason, they can be potential sources of danger in my cybersecurity system. Cybercriminals are looking for such gaps and opportunities, using infinitely insidious methods in many forms of phishing.
Effective human resources also raise serious questions. An omniscient, forward-thinking cyber specialist does not exist in the same way that wizards do. There are specialists in Hungary as well, and there are payment requests and well known limited availability. Yes, they are few, and we will find gold on the banks of the Danube sooner than an IT security specialist at an affordable price. The bottleneck has already been found in our formula. Depending on the size of your organization and your IT security system, only one specialist may not be enough.
Of course, the need for human resources can be reduced if, for example, we do not use the solutions of 25 manufacturers, but move towards standardization. Even in a relatively standard security system, there are plenty of areas of technology that require different professionals. And of course SIEM, SOAR, ISE, SASE, XDR, EDR, and other solutions do not only obtain information, analysis data, alerts and recommendations from their own “wellhead”. So there are plenty of liaisons with other 3rd party solutions, thank goodness, security development companies have long realized this.
HOW CAN THE RECOMMENDATIONS BE ADDRESSED EFFECTIVELY?
And here comes the point: machine learning and artificial intelligence. Without them, an advanced security system could not exist today. Not to such an extent that if every person on Earth were a cybersecurity specialist (this is an anomaly, of course, because then there would be no hackers or malicious artificial intelligence or bad bots), there would not be enough monitoring, analysis and response capacity for the current level of cyber threats and vulnerability testing and investigations. Only machine learning, the control and analysis of behaviors, operations, processes, and artificial intelligence can provide unique protection for these. No two companies are completely identical in terms of cybersecurity, but there are billions of vulnerabilities, countless forms of threats, and last but not least, there are just a small number of security professionals. It would be impossible for one or two specialists to monitor the IT behavior, total data traffic, state of data storage, endpoint devices, application vulnerabilities of even a small company’s users, and compare all of them with data coming from organizations researching cybercriminals and sharing information on defense. It would be impossible to build reactions and responses to the observations and incoming cyber defense data – of course, after careful analysis.
Well, that’s why the deployment of machine learning and artificial intelligence in the areas of IT security is inevitable. And of course in other areas with high computational and analytical needs.
However, the good news for company and organization leaders is that these services are available. And today, it’s much cheaper than creating a well-organized, omniscient professional SecOps team. Conversely, there are expensive but super-duper SecOps teams, and red, blue, and purple security development teams to help develop machine-learning and AI-driven solutions and support remote operation of systems. As a result, it is enough for an organization to deploy an efficient, managed and well-segmented IT system with a ZeroTrust strategy, powered by a SASE approach, and monitored with advanced SIEM-XDR system. Of course, there will still be damages, data leakages, and even successful attacks. However, the use of intelligence can provide much faster responses and more effective remediation.
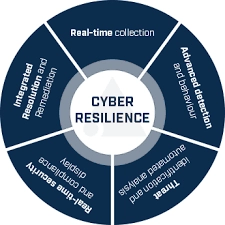
CYBER RESILIENCE
No matter how strong a company’s security is, it is always exposed to cyber attacks. Cyber security deals with these attacks. Cyber resilience is the preparation and implementation of strategies that enable operations to withstand these events. This is a precaution that works before, during and after cyber attacks. Cyber resilience is actually a series of proactive security measures. These strategies designed around the IT infrastructure increase security in the system and reduce the potential for cyber attacks. A successful cyber attack causes material damage and destroys the reputation of the organization, while with cyber resilience these effects diminish.
So today, the question is no longer whether an organization will be harmed, but how much it will be effected. The attitude, that I have a firewall and antivirus, I have multi-factor authentication for accesses, I have a super-secure VPN, I encrypt all my sensitive data, and they’re stored offline anyway, so “the most I am secured” long-expired approach. Self-confidence is a good and healthy thing, just not effective against cybercriminals. They are not concerned with the faith of those involved in the defense, but with how to get into a network, how to steal keys, how to obtain data, possibly encrypt or, wipe it, and how to do damage or blackmail money.
CONCLUSION
So cyber-resilience can be a good direction for any country, for any organization, but it still seems to be alike a struggle against climate change. Everyone tells us what needs to be done, what can be done, but no one can to tell us, when it becomes an effective and common solution. Proactive cyber defense is a similar struggle, there will be those who do a lot against the constant threats, there will be those who don’t really. The difference in the fight against cybercriminals and climate change is that there will be those who can “benefit” from it because they are prepared for attacks, and there will be those who will cost a lot for a lack of considered protection. Therefore, we are not persuaded to emphasize that the most important thing is to create a system that is aware of our own “weaknesses” and that has intelligent responsiveness that can avoid greater damage. A good cybersecurity solution doesn’t show that everything is OK now, but what you need to do to stay safe today and tomorrow.
Fortunately, this no longer requires super-trained, in-house teams, just a responsible leader who adheres to the system’s recommendations to the maximum and takes the necessary steps within the organization. Thus, machine learning and artificial intelligence-driven solutions can provide a significantly higher level of protection with significantly less human resource effort and budget.